Bytectf 2019 s390 Writeup
Category: RE
Score: 833
Solved: 5
在上一章中已经讲到将IBM ZOS S390搭建好了,在hercules上安装了Ubuntu 18.04 s390x。
在本文中将讲解如何对其进行静态分析和动态调试,以及IBM z Architecture的汇编资料。如果你有更好的想法,欢迎与我交流。
由于目前的主流反编译器、反汇编工具如IDA、Ghidra、radare2、objdump均无法有效的跨平台反汇编,更没有办法调试,因此我选择搭建s390环境,并在该环境中分析这个elf文件。
搭好了环境,先运行一下:
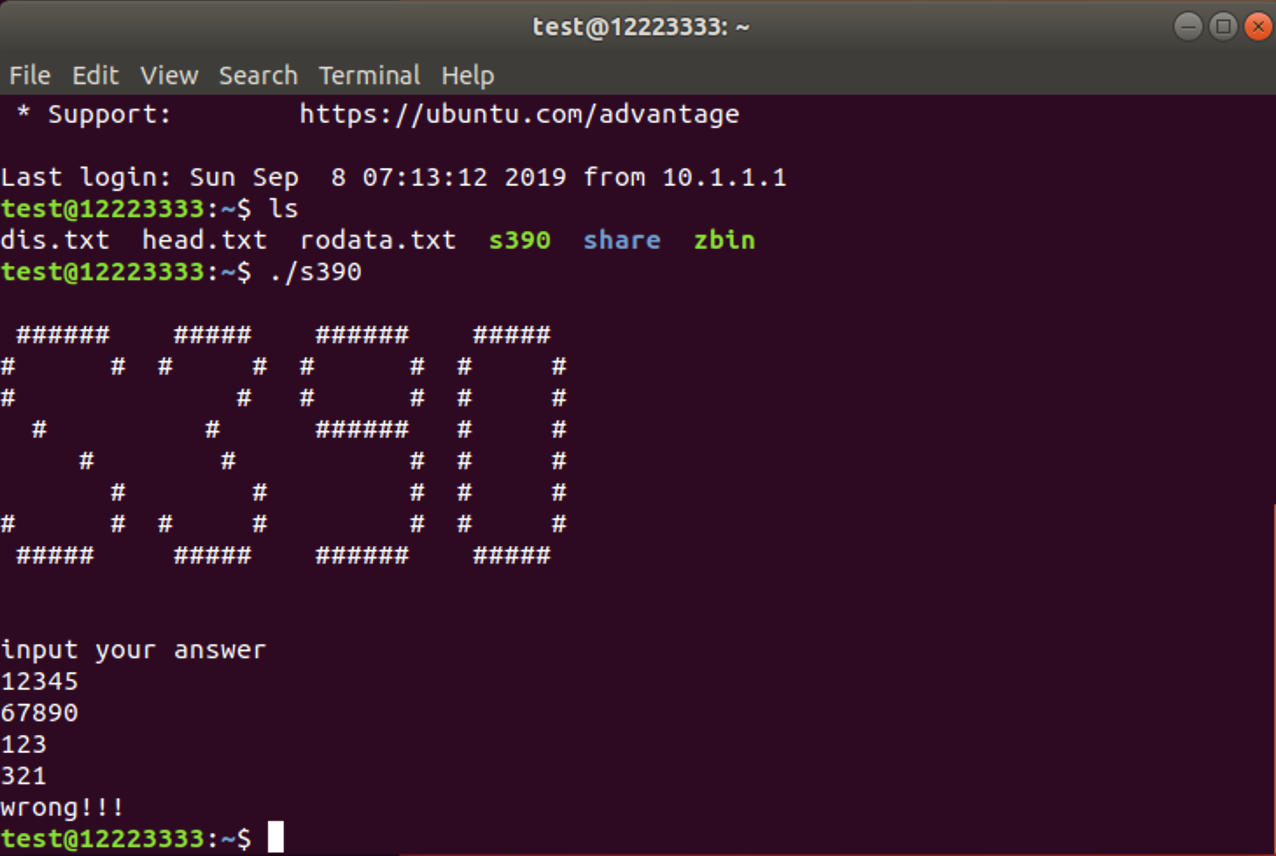
动态调试
直接用s390上使用apt-get install gdb,但该版本的gdb有点问题,虽然能够调试,但无法使用step、next命令,只能通过b、c来调试。可能的解决方案:下载gdb源码,在s390上编译。(在虚拟机中的虚拟机中编译,很慢很慢…)
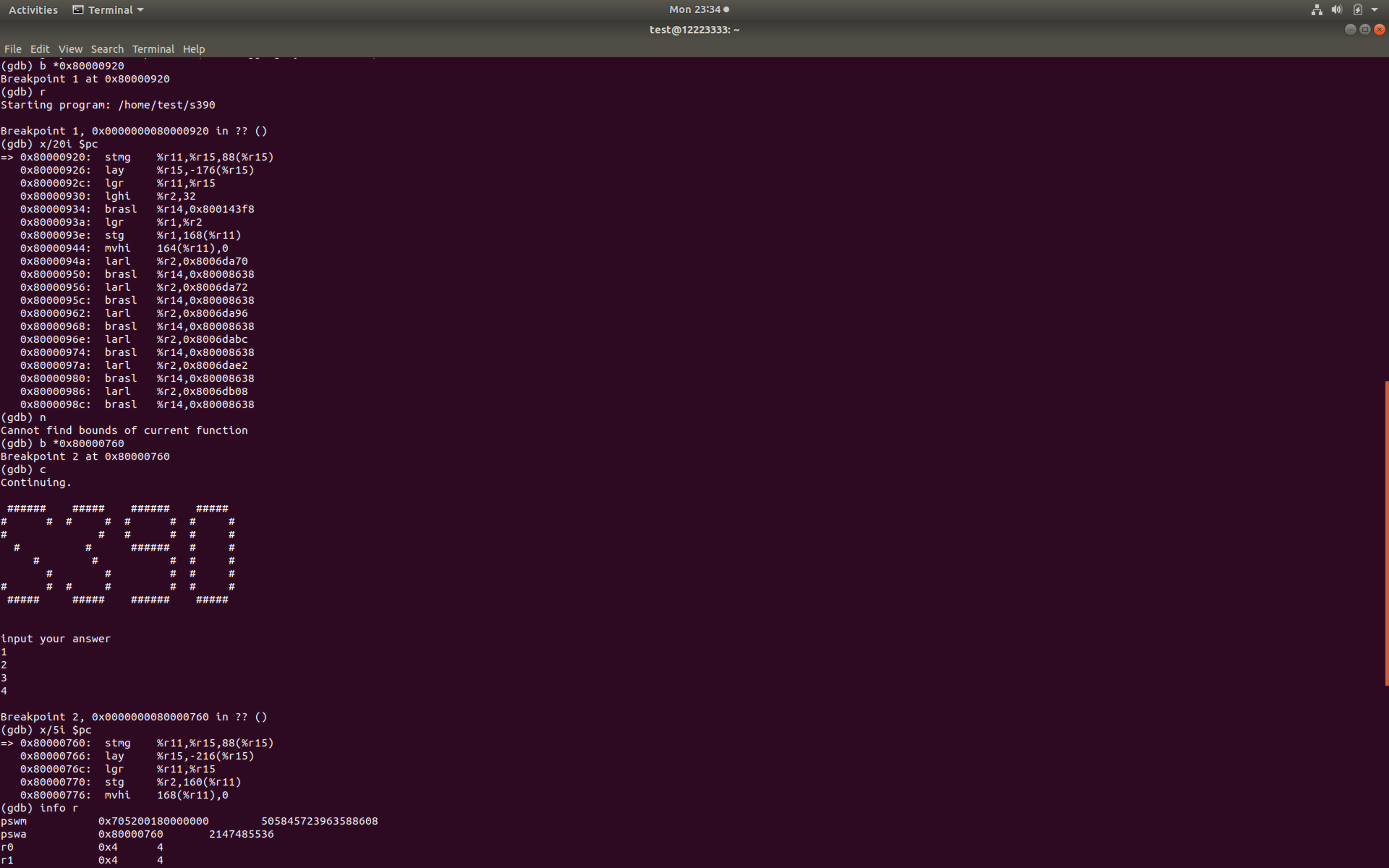
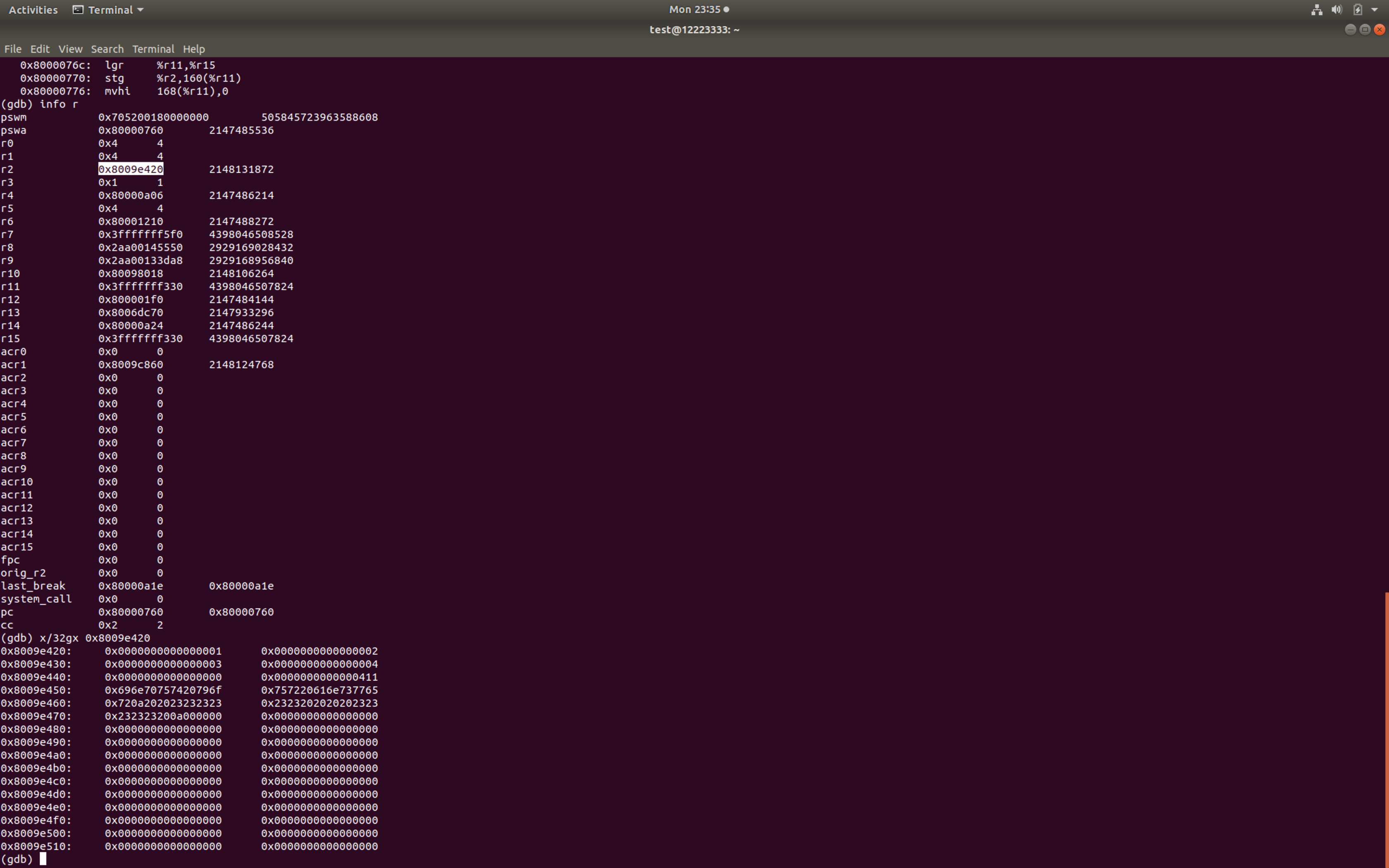
静态分析
查看所有段
1 | objdump -h ./s390 |
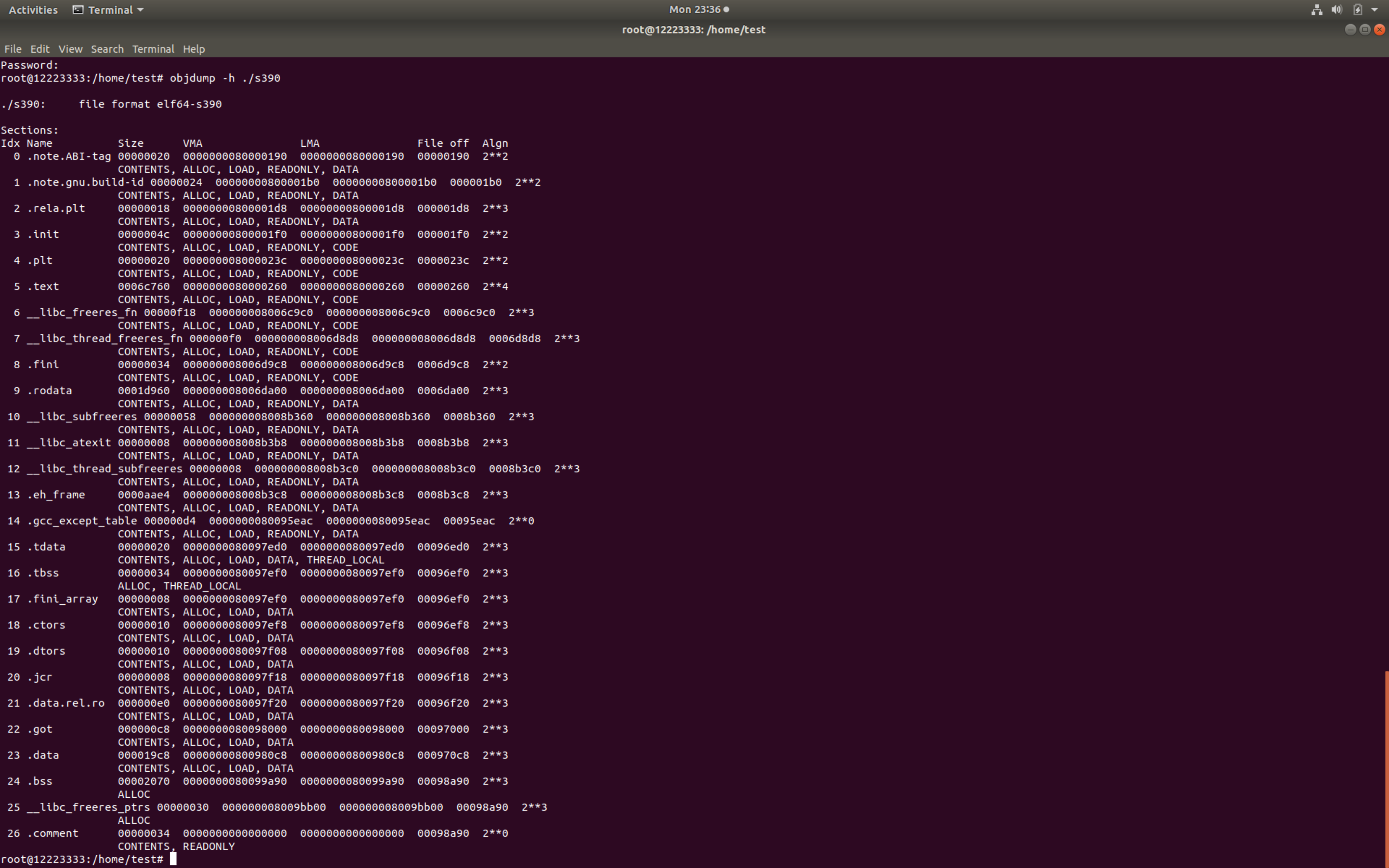
使用objdump反汇编,并导出到文件
1 | objdump -s ./s390 > dis.txt |
使用objdump把rodata段dump出来,并在编辑器中打开,
1 | objdump -j .rodata -s ./s390 > rodata.txt |
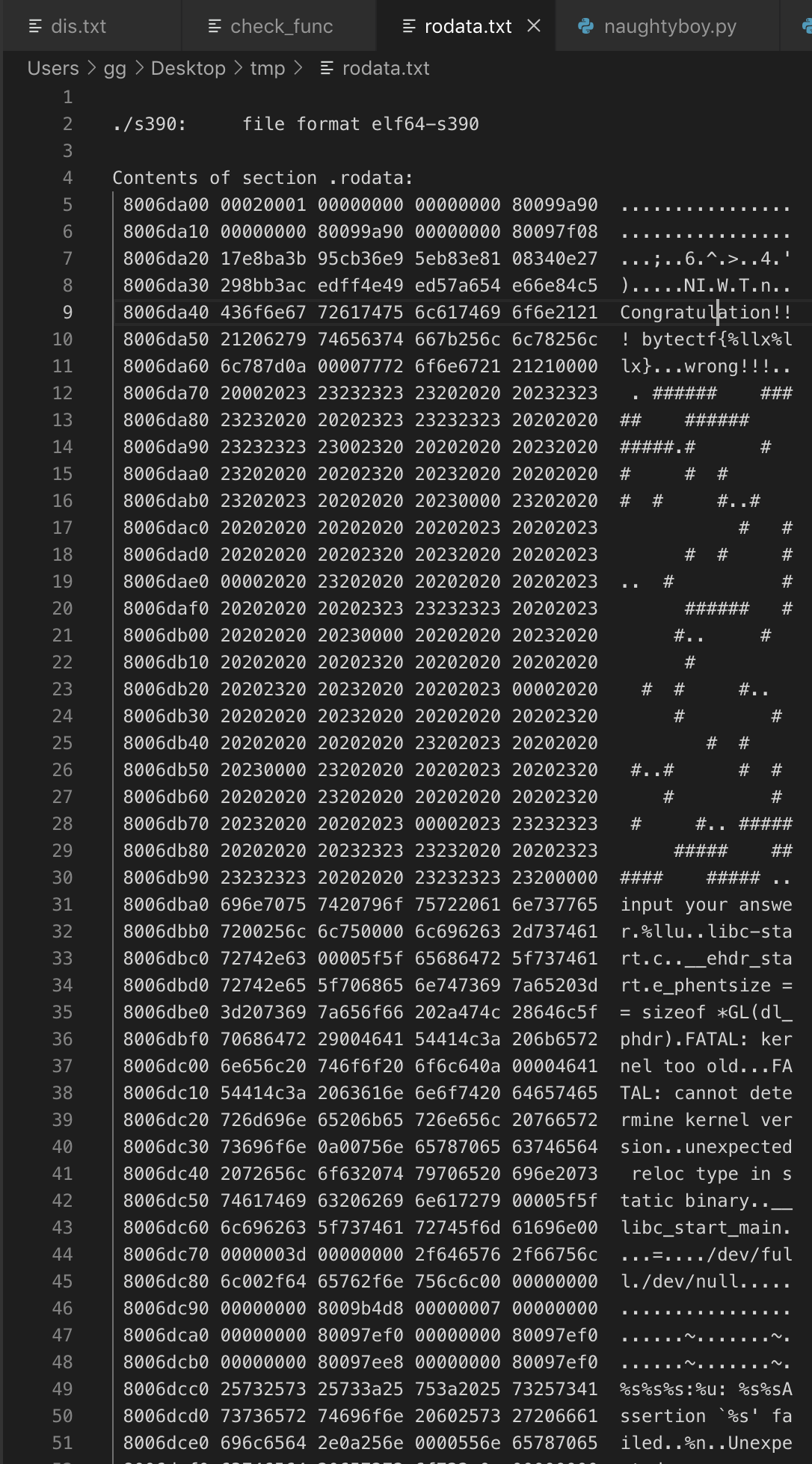
定位到几个关键字符串地址,在反汇编代码中查找,顺利定位到main函数:
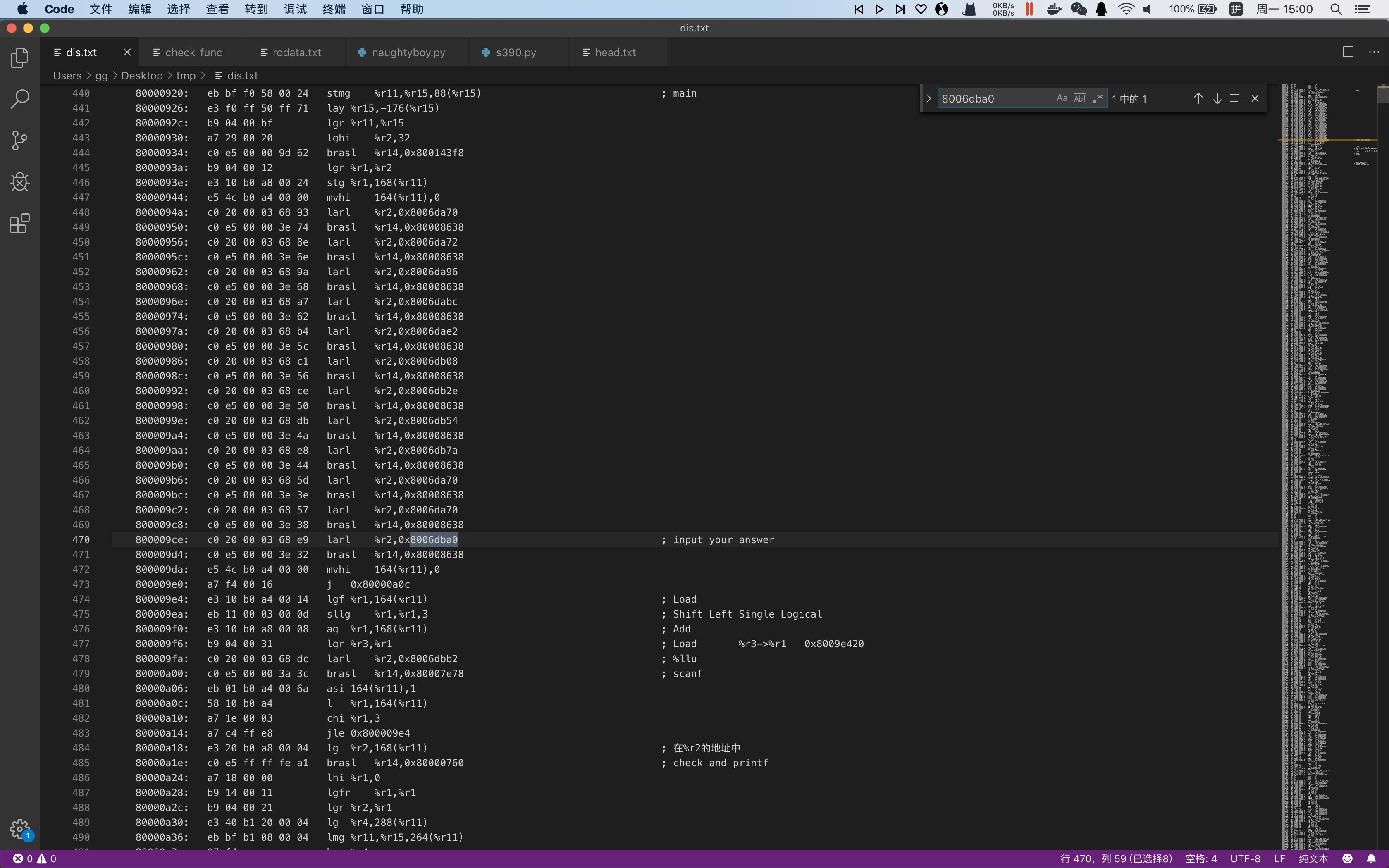
对照http://www.tachyonsoft.com/inst390m.htm了解汇编指令,并标注其含义。
同时进行动态调试,发现循环4次scanf(“%llu”, &(%r11+168)+8*(%r11+164)),输入4个数字(%r11可视为栈指针)
main函数(0x80000920):
1 | 80000920: eb bf f0 58 00 24 stmg %r11,%r15,88(%r15) ; main |
接下来call 0x80000760,并在该函数中检查输入并输出结果。(Architecture z的汇编与MIPS类似,brasl为跳转并链接,即为call)
最主要的是0x80000760函数,不过现在我们有汇编代码、有参考手册、有gdb动态调试,分析其功能只是时间问题。以下是我对0x80000760函数的分析:
1 | 0x80000760: eb bf f0 58 00 24 stmg %r11,%r15,88(%r15) ; Store Multiple ; check and printf |
有一个五操作数指令risbg %r1,%r1,63,191,0手册上解释其功能为Rotate then Insert Selected Bits,不太理解,不过根据动态调试的结果,其功能为取最低位放回%r1,等价与%r1 = %r1 & 1
分析check函数0x80000760可知其为一个快速幂算法,对四个输入进行快速幂运算,得到9533次方,与rodata中的密文进行比较,输出结果。
解密脚本
1 | target =[ |
其他
可以在ubuntu上安装gcc-s390x-linux-gnu,交叉编译静态链接有符号的二进制文件,帮助我们识别无符号elf中的libc函数,如scanf。
参考https://packages.ubuntu.com/xenial/gcc-s390x-linux-gnu,可使用`apt-get install gcc-5-s390x-linux-gnu`安装交叉编译器。
导出来的txt:
参考资料
z Architecture汇编手册:http://www.tachyonsoft.com/inst390m.htm
zpwn200题解:https://blog.dragonsector.pl/2014/02/olympic-ctf-2014-zpwn-200.html
zbin500题解:https://blog.dragonsector.pl/2014/02/olympic-ctf-2014-zbin-re-500.html