2020 腾讯游戏安全技术竞赛 初赛-Android-Writeup
java层和libcrackme.so中逻辑很简单,调用libgoodluck.so中的Tell_me_the_key检查输入字符串
Tell_me_the_key函数逆向:
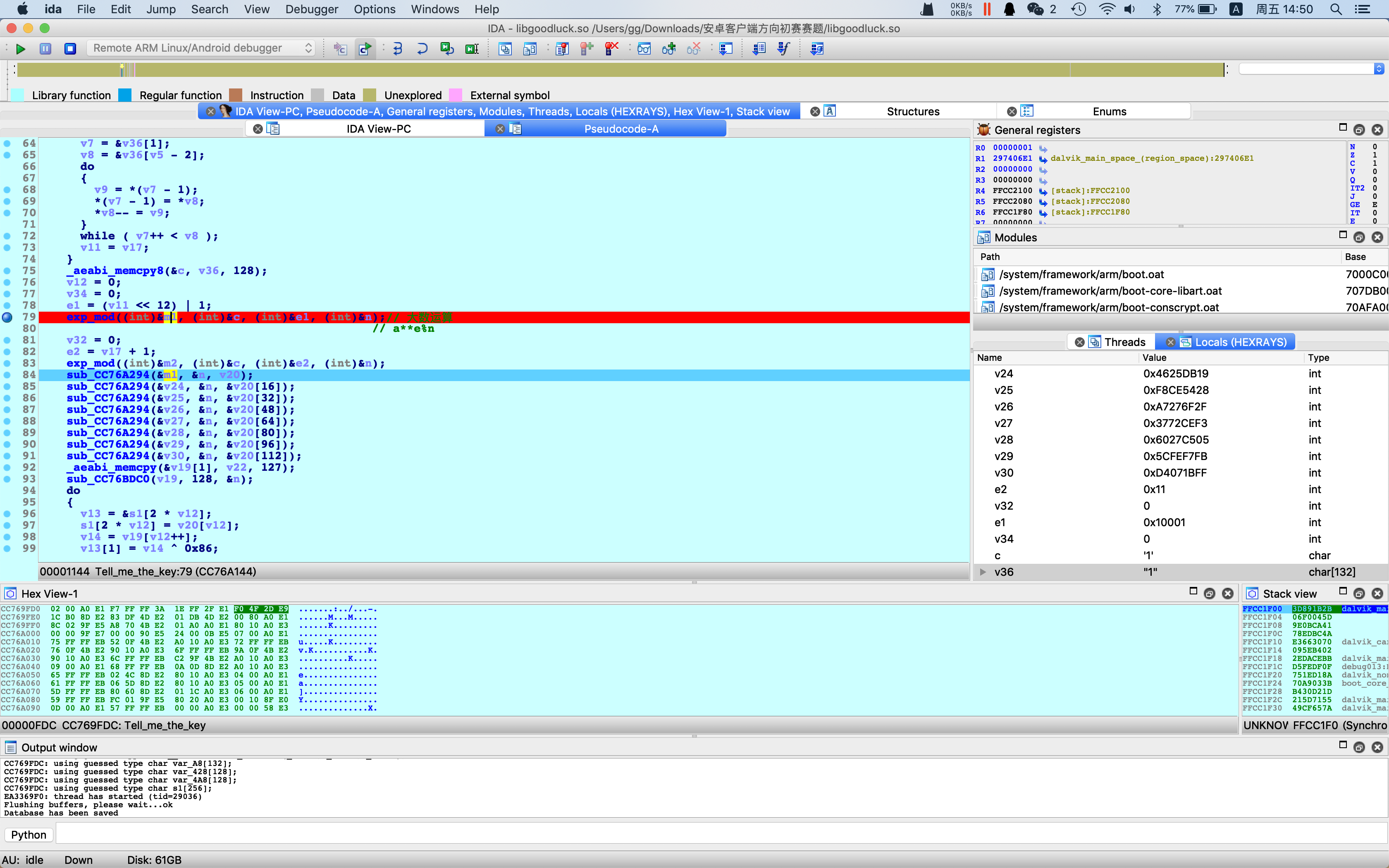
构造输入为’1’,与调试结果匹配,验证快速幂算法,以及大数存储形式
1 | import binascii |
1 | exp_mod(&c2, &m, &e2, &n); |
n为1024bit,通过共模攻击,恢复m。
恢复C1:
sub_CC76D294函数:算法结构类似AES。
与普通AES加密算法不同的是:roundkey的生成过程、SBOX使用时异或了0x6B、ciphertext出来的时候异或了0x27。
求逆SBOX:
1 | def get_inv_SBOX(): |
AES解密(详见aes-128.cpp),得C1:
1 | v20_m = [ |
恢复C2:
sub_CC76EDC0、sub_CC76EA98函数:
控制流平坦化,动态调试,sub_CC76EDC0比较好分析,4byte4byte传入sub_CC76EA98。
sub_CC76EA98分析:
根据0x61C88647,推断出为类TEA加密,动态调试发现轮数没有32轮
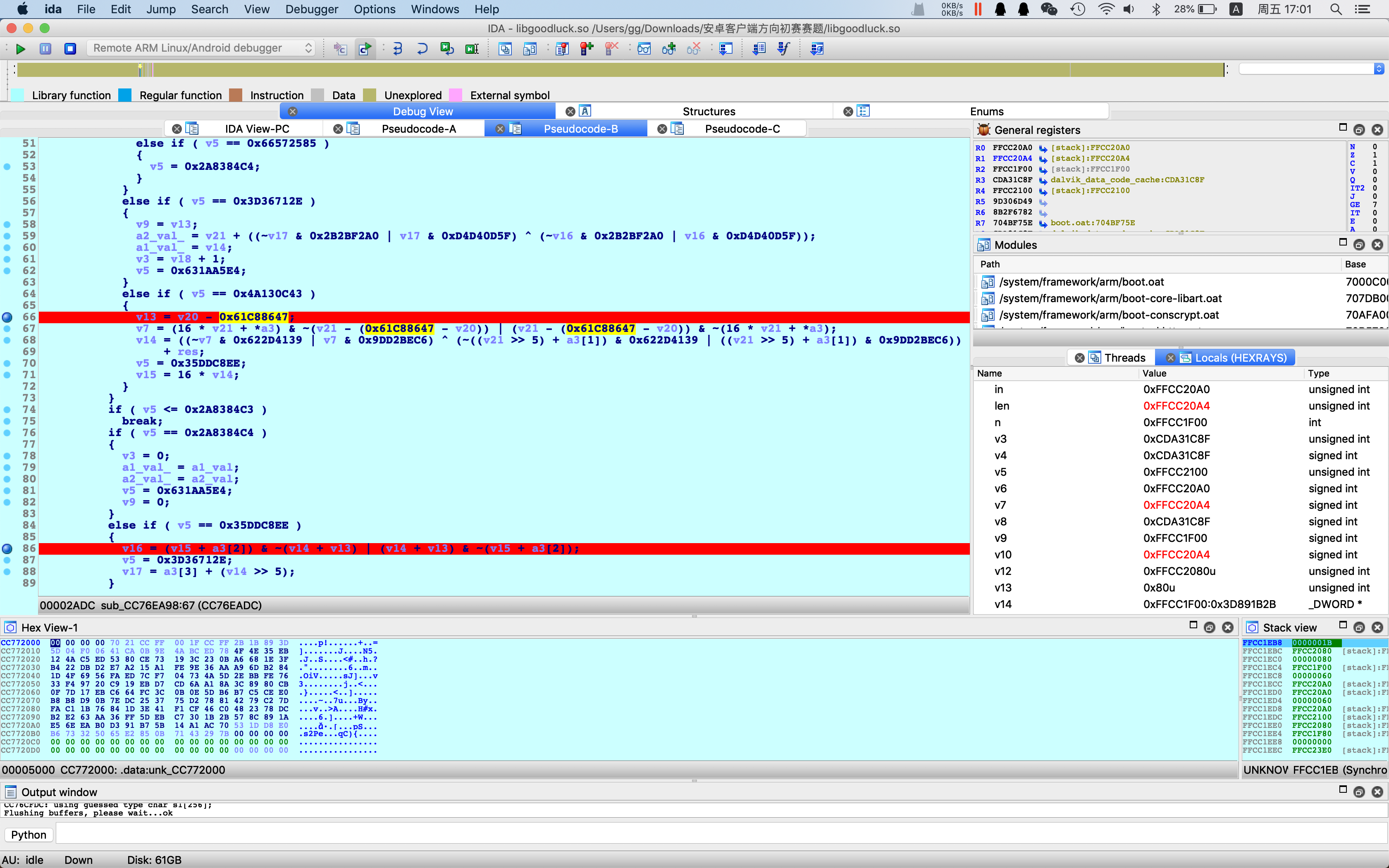
验证了一下,动态调出来的值为TEA中间变量,确认算法为8轮TEA。key为n的前4个uint32。(代码详见tea.cpp)
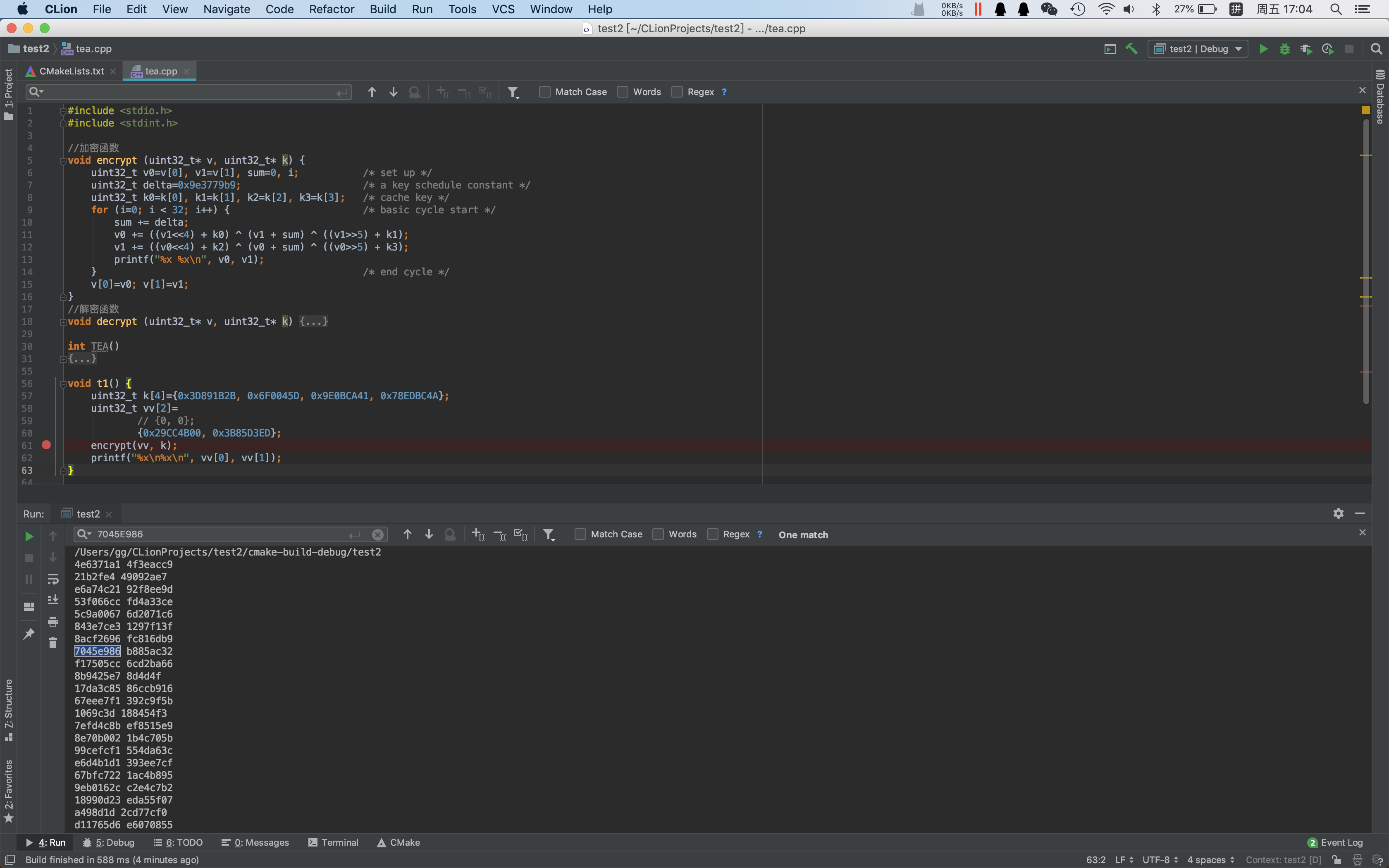
解密得C2
1 | v19_m = [ |
共模攻击:
C1最低位为止,爆破可出
1 | import gmpy2 |
得flag:
1 | Tencent_GSLab_Sec_2020 |