DDCTF 2020 Writeup
DDCTF 2020部分题解
名次:第二名
队伍:Darkkkkkk
队友:JrXnm
Web
Web签到题
验证auth拿到client
访问http://117.51.136.197/admin/login, username=admin&pwd=123456, 拿到一个jwt的token, 密钥是123456
拿去jwt.io, 修改一下Role 改成ADMIN, 改个时间戳
去访问http://117.51.136.197/admin/auth
这时可以拿到一个client二进制文件
client 逆向
golang编译的无符号ELF,使用GoUtils2.0恢复符号信息,结合命令行输出的提示以及wireshark抓包的结果,发现其向“http://117.51.136.197/server/health”、"http://117.51.136.197/server/command" 发了两个请求,根据其发送的请求逆向binary,发现其使用”DDCTFWithYou”作为key,对”command|timestamp”做hmac-sha256后base64 encode
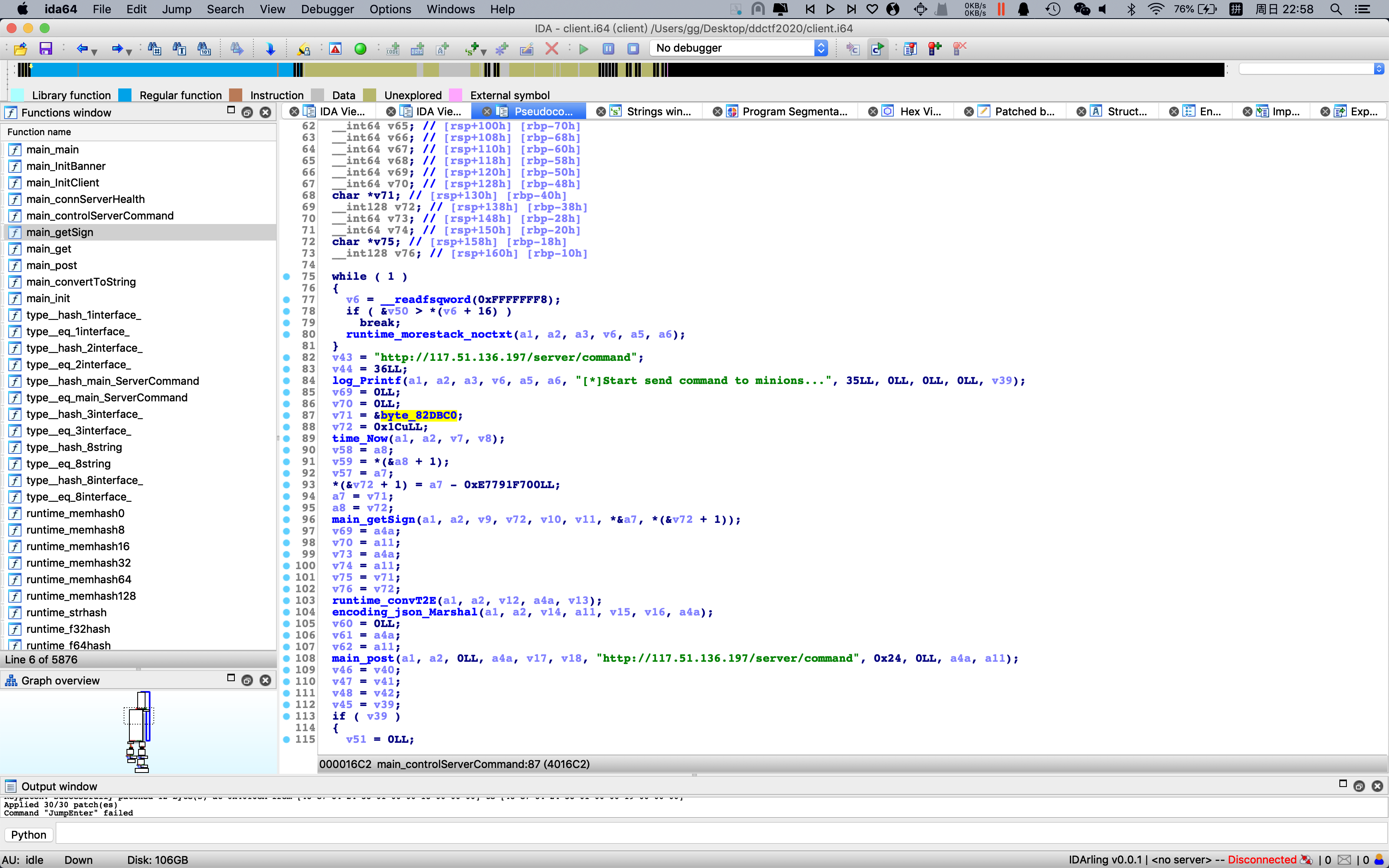
写出模拟发包脚本:
1 | import hmac |
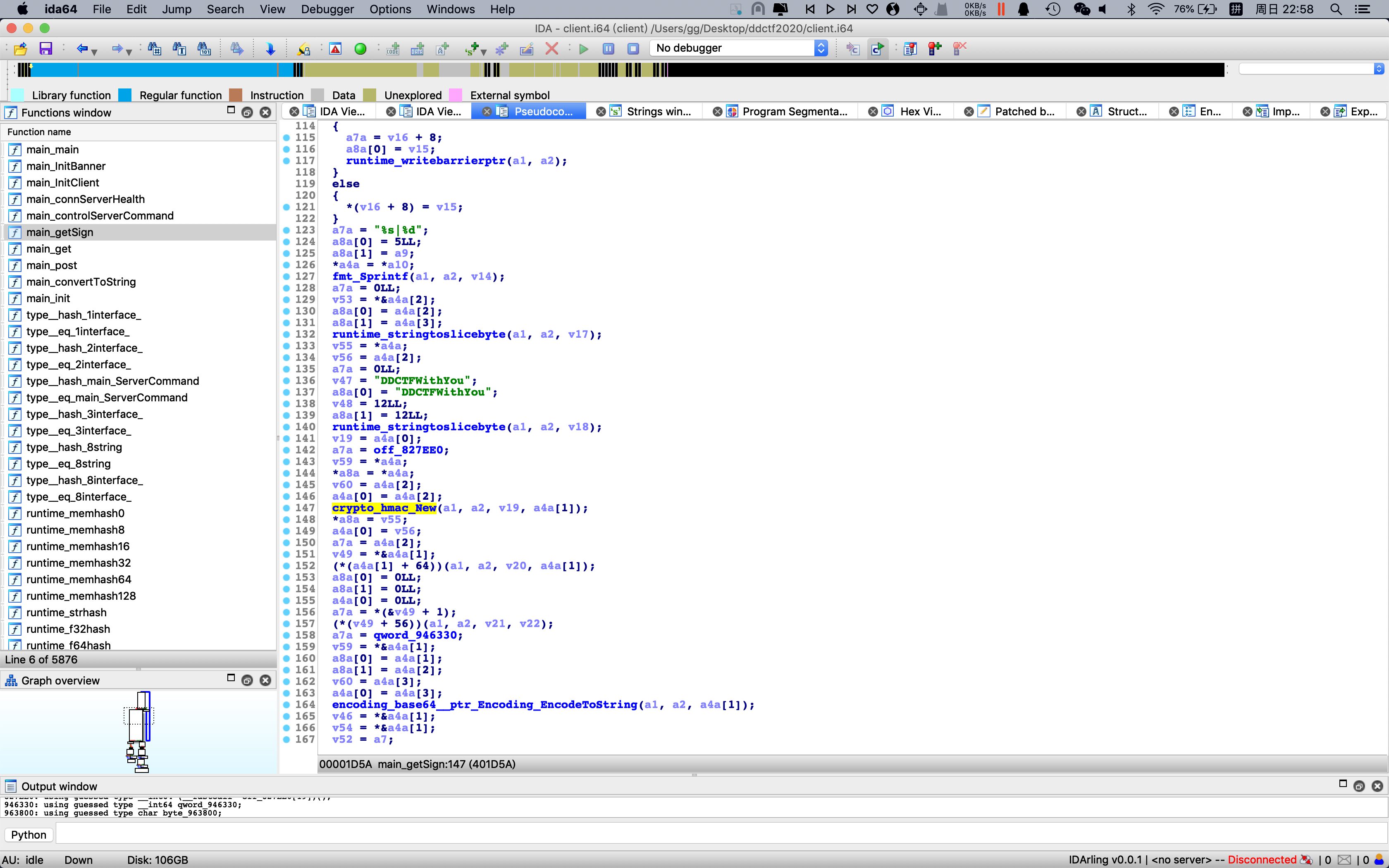
在这里可以发送command执行,测试这个执行的command不是shell命令也不是go代码,而是java的spel注入
1 | import hmac |
有一些限制,但是读文件没有问题,代码如上,直接读flag。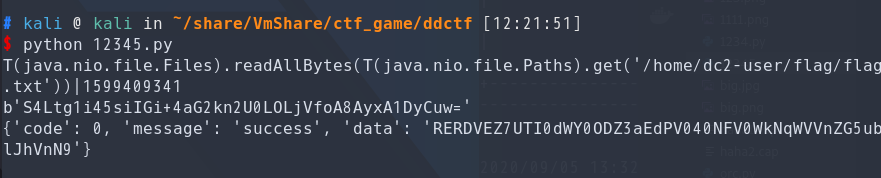
DDCTF{Q24uf486whGOWN44UtZCjYUgdnnnRaVs}
Reverse
Android Reverse 1
静态分析+动态调试识别算法为AES ECB 128,key为”1234567890123456”、可能为TEA、MD5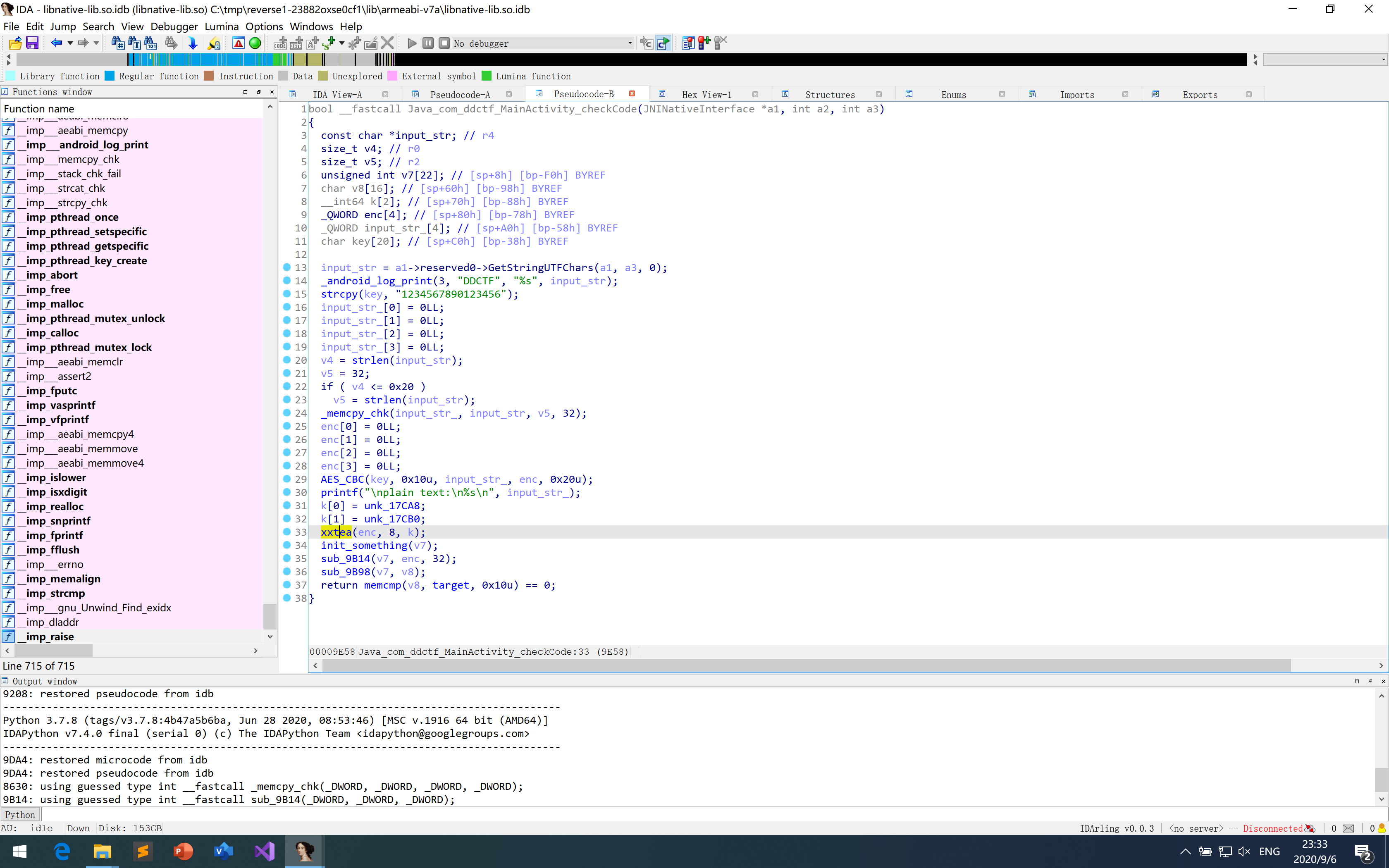
TEA脚本算出来不大对(可能是我脚本问题),不过发现binary中的类TEA函数通过判断长度的正负以决定进行加密or解密,于是可以断在xxtea(0x9208)处,将buf修改为提示中md5的输入,R1长度8改为0xFFFFFFF8,即可复用binary解密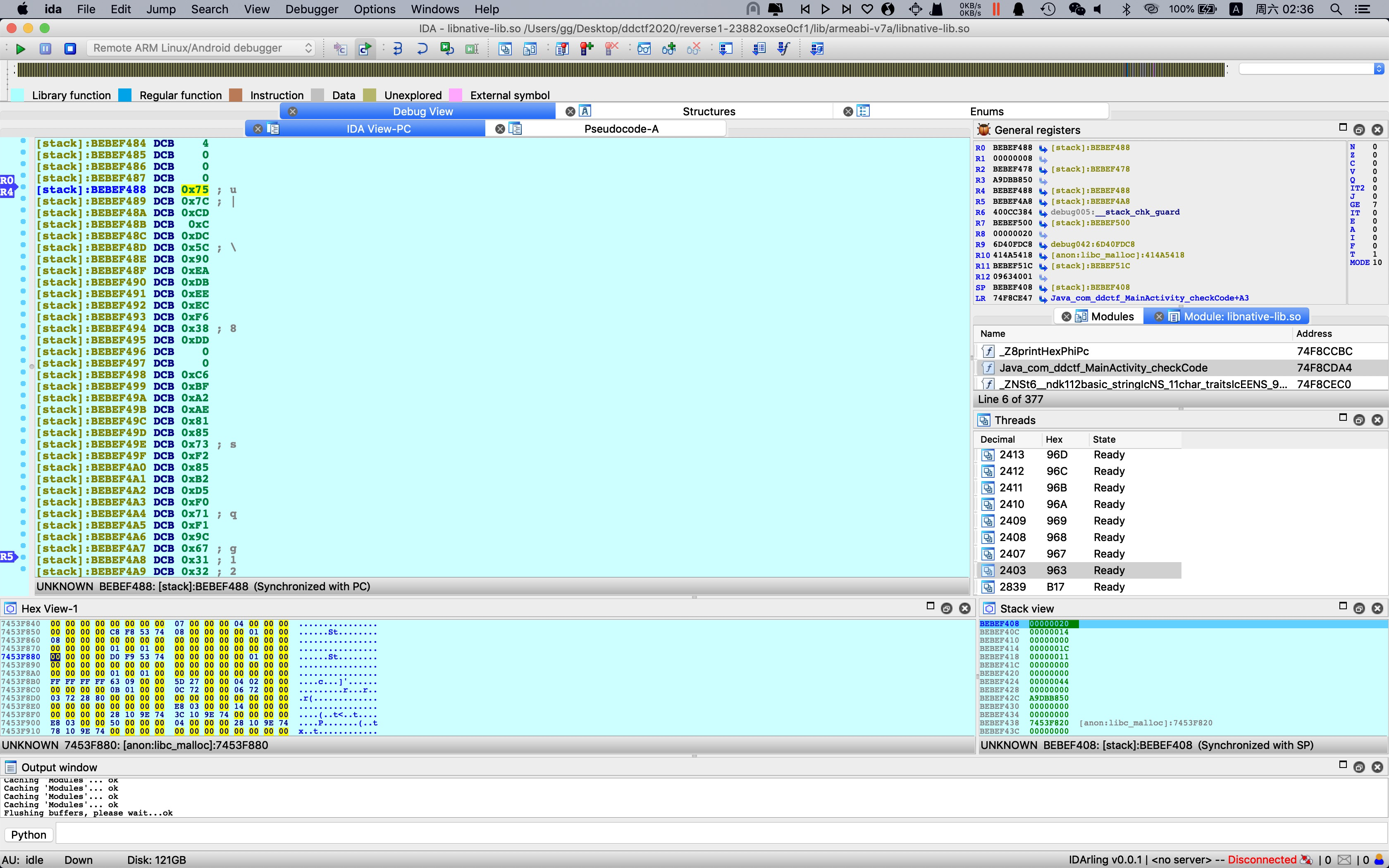
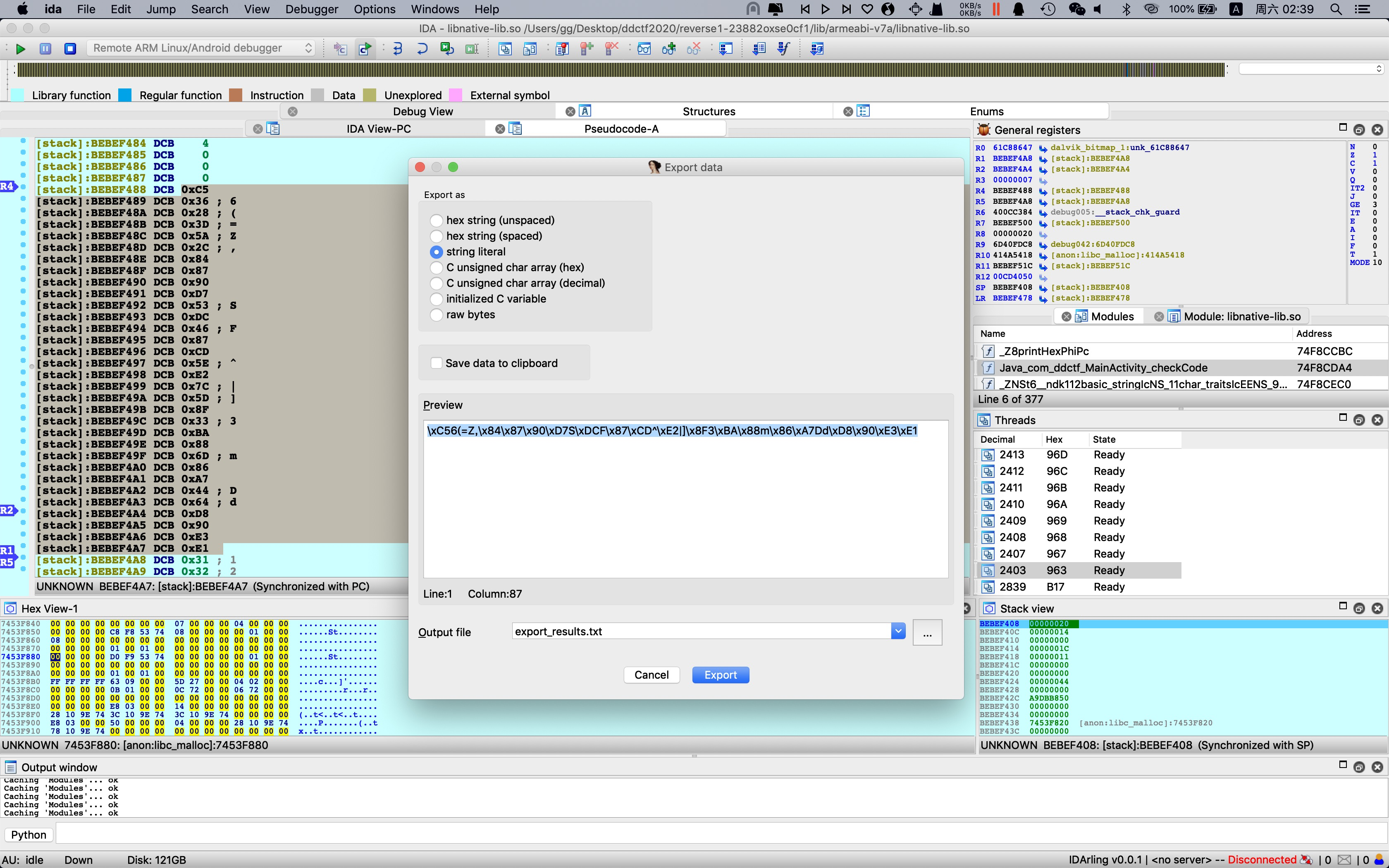
随后buf内存dump出来,用AES解密即可
1 | from Crypto.Cipher import AES |
DDCTF{wsxsdf0987!}
Android Reverse 2
静态分析发现与第一题是一套源码编译的,加了字符串加密和部分控制流平坦化,结合动态调试直接dump字符串,做法与上题类似,类XXTEA前下断,patch内存,修改R1,复用binary解密,随后AES解密,得flag
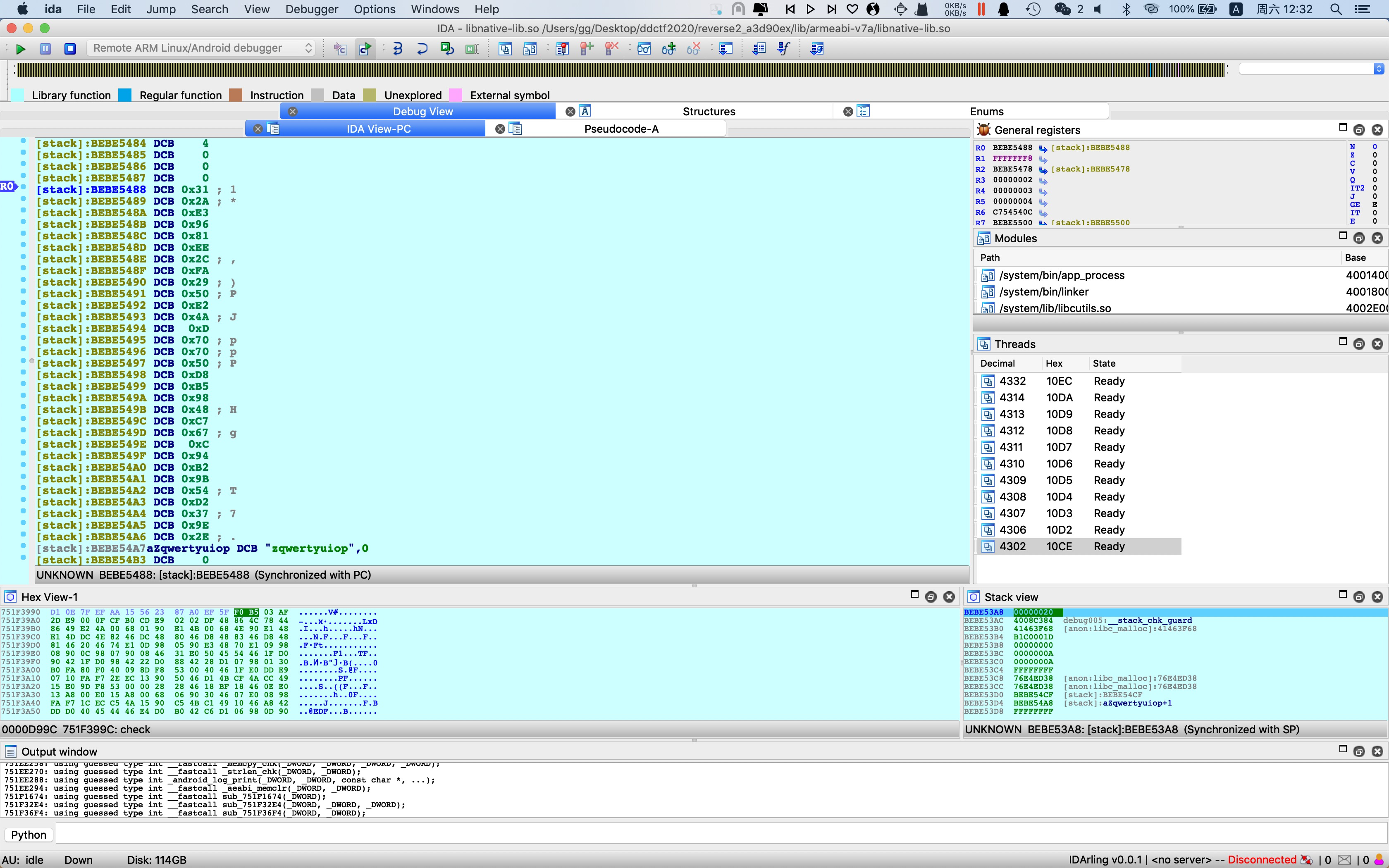
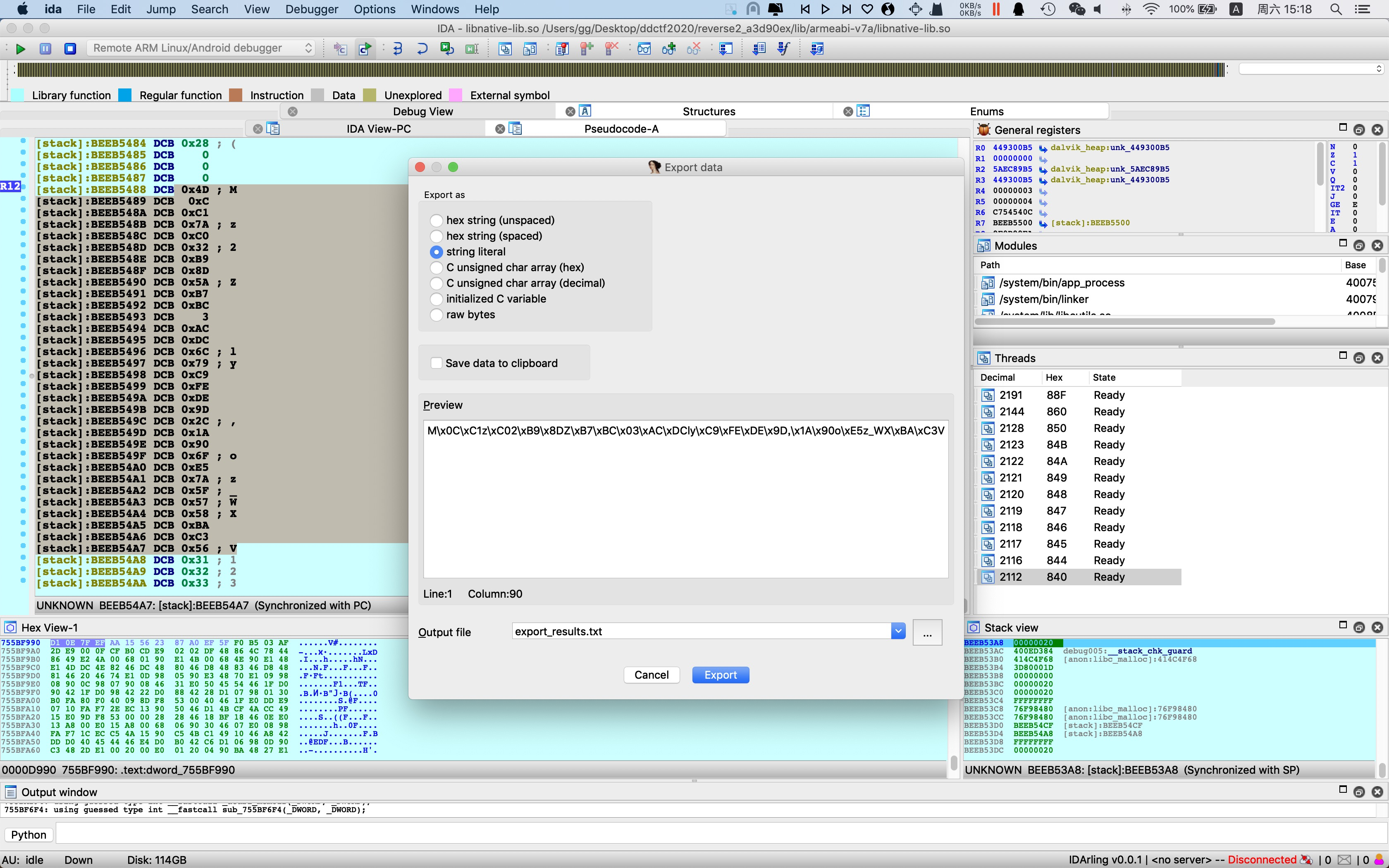
1 | target = [ |
DDCTF{FiNal CuP$}
Android Reverse 3
初步静态分析,发现:
- init_array 中字符串解密
- JNI_OnLoad 中pthread_create起了子线程检查”/proc/{pid}/status”中的TracerPid
- JNI_OnLoad 中动态注册crypt函数
与re2相比,也有字符串加密,更强的控制流平坦化,还加入了反调试。
使用patch过kernel(使TracerPid永远为0)的安卓手机进行调试,字符串dump出来发现其访问http://117.51.142.44/getPW 拿key。通过findcrypt发现AES SBOX。
试了几个静态去平坦化的工具,发现效果一般,直接在check(0x4FD4)函数中的数个可疑处下断点(getPW函数、AES setup、AES encrypt、sha1),动态调试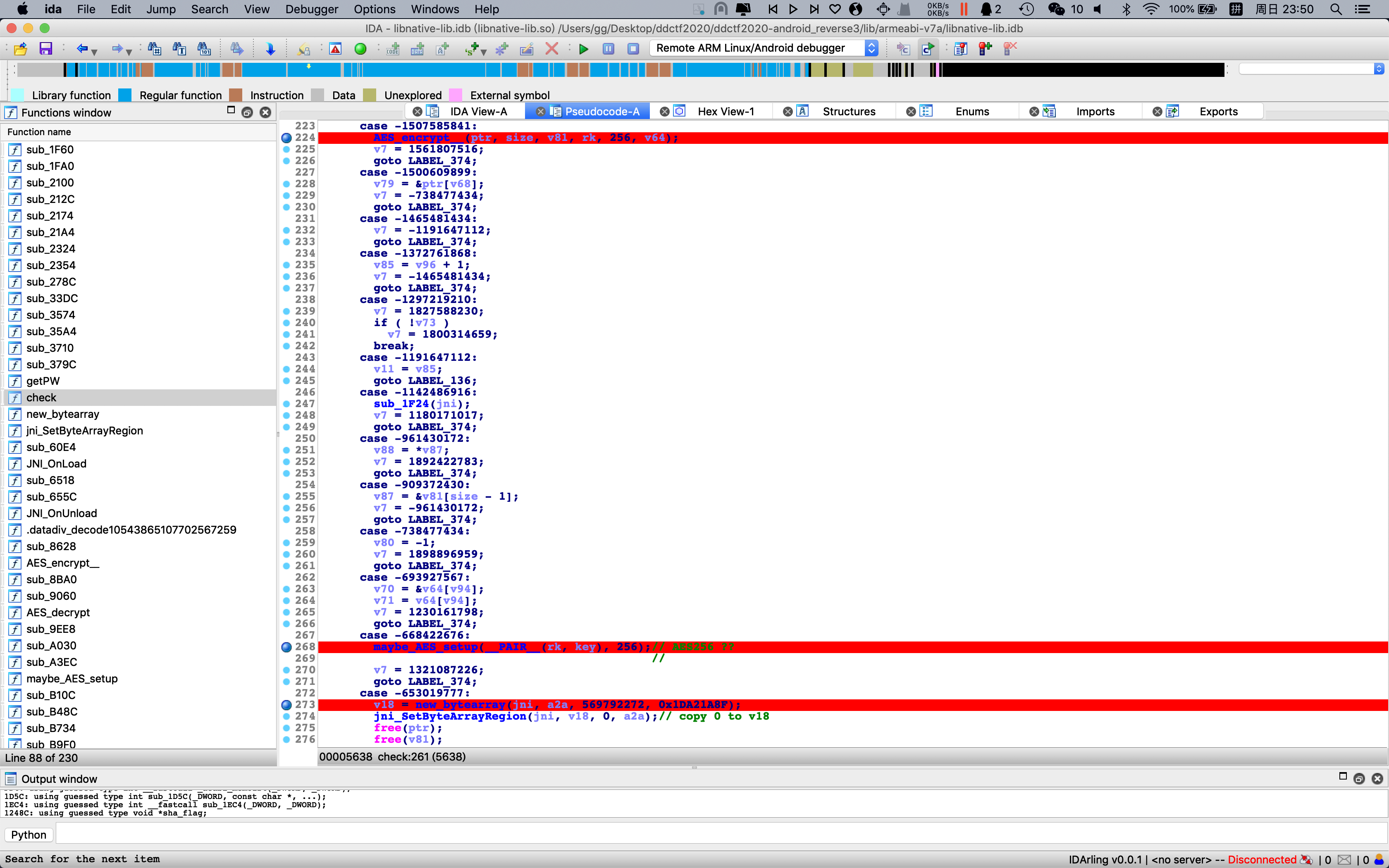
发现flag的检查算法只是从网上读了一个key,明文padding后AES CBC 256加密,SHA1后与常量比较
写出python正向脚本
1 | AES_key = [ |
尝试使用python多进程爆破,速度太慢,放弃。
使用c编写多进程爆破,脚本如下:
1 | // |
64核机器上跑,运气比较好,没多久就跑出来了
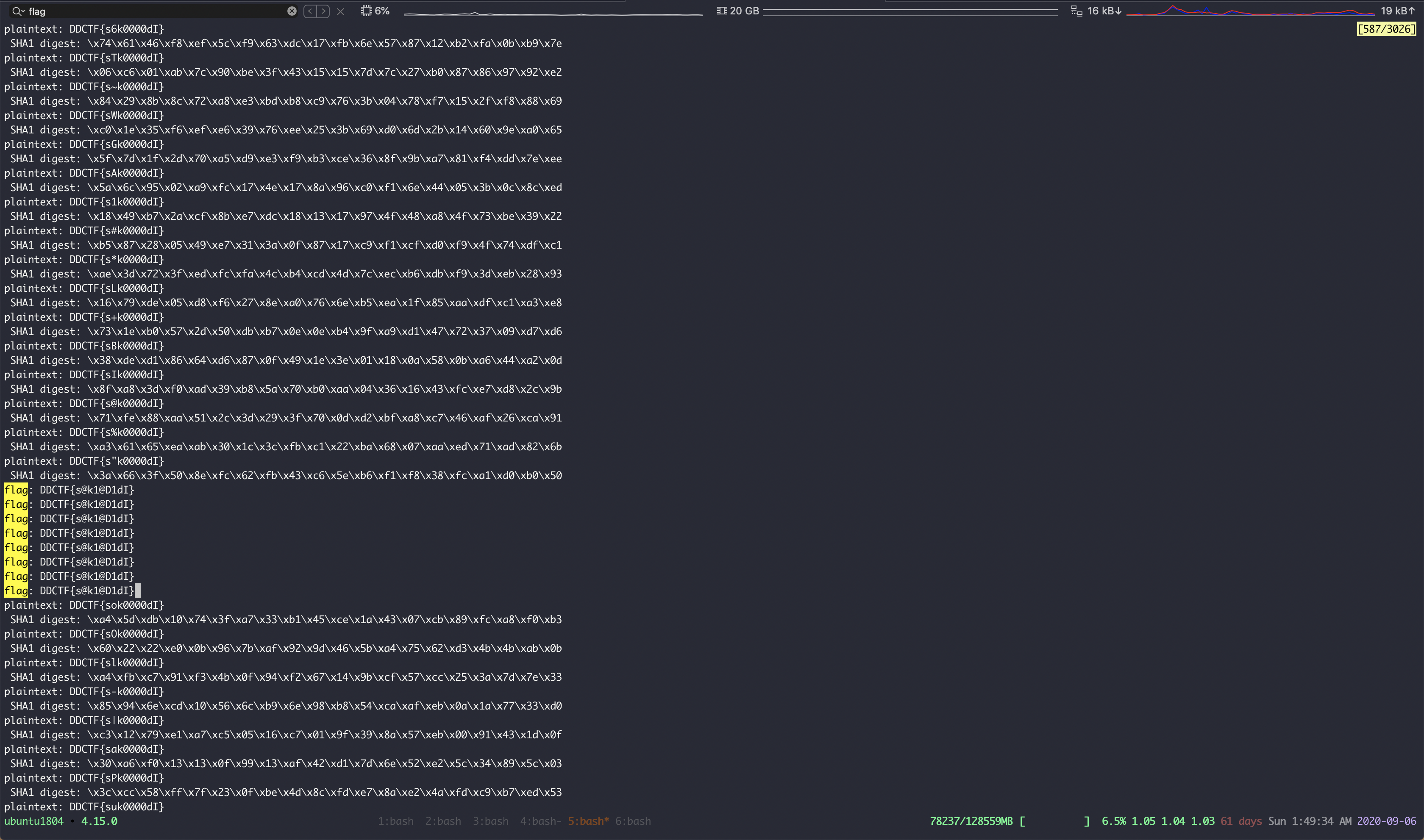
DDCTF{s@k1@D1dI}
MISC
一起拼图吗
筛选出修改的图片,发现数量较少,只有二十来张,可以手动拼:
1 | from PIL import Image |
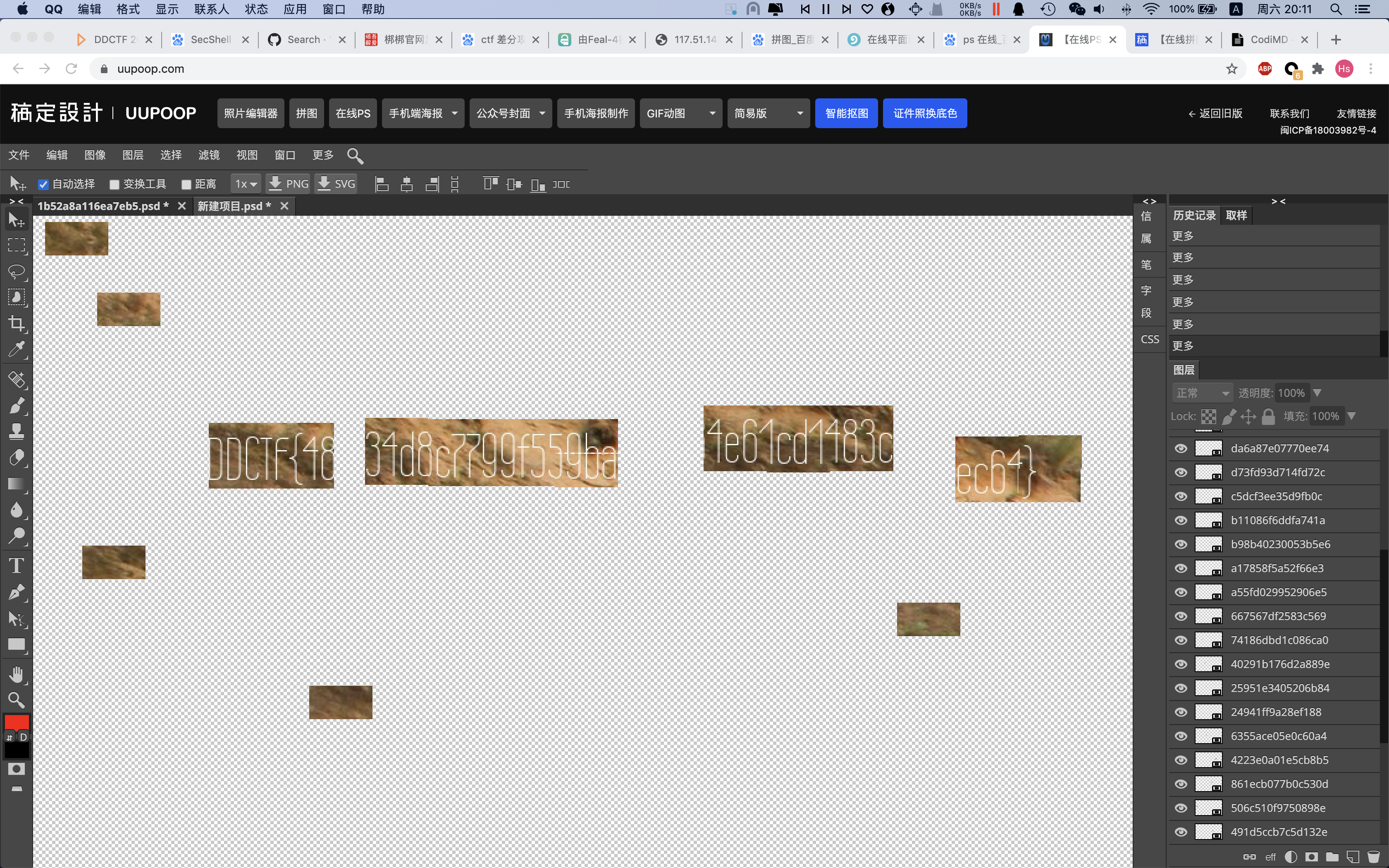
四段 中间两段顺序不太确定
DDCTF{48、 34d8c7799f559ba、 4e61cd1483c、 ec64}
尝试提交,flag为:
DDCTF{484e61cd1483c34d8c7799f559baec64}
decrypt
发现k3和k4可以合并,给了数字形式的两对明密文对,密文异或可消除k3 k4,只剩k0 k1 k2三个12bit数字,爆破空间为2**36,可以接受,64核直接爆破:
1 | # Define constant properties |
DDCTF{4458C756F7BF4F5324060909F7944054}